Certificate Management
Certificate management in DMA is designed for users with a deep understanding and experience of certificates and their use on Cisco collaboration devices. It provides a set of tools to reduce the time and effort required to store, deploy, and manage the lifecycle of certificates. We strongly recommend that anyone using this feature reads this section first and take the time to read the relevant Cisco collaboration device reference materials for certificates.
Important Information
Cisco has broken certificates down into two types, Service & Custom.
In the UI you can see that service certificates can be assigned services; these are also directly assignable on upload in DMA:
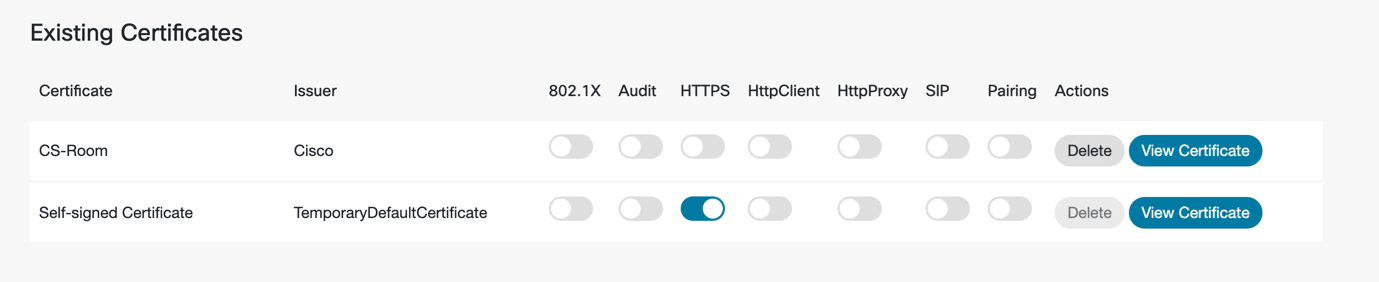
Custom Certificates do not have types. In DMA, as we are deploying the certificates we have introduced a mapping type.
This type dictates how this certificate will be deployed.
One To Many (1:M) - these are certificates that can work on multiple devices
One to One (1:1) - these are certificates that are only valid or specific to a certain device. Certificates contain a Common Name ( CN ) or Subject Alternative Names (SANs) that include IP addresses or FQDNs for a certain endpoint.
Custom Certificates are always 1:M - these are usually Certificate Authority Certificates that are on the devices so it can talk to other IPs. For example, in DMA the Server Certificate is a CA certificate we put on all the endpoints so it can talk to our VQCM instance via feedbacks.
Service Certificates can either be 1:1 or 1:M - if a certificate includes a common name for a certain device i.e CN=192.168.20.80 then that certificate will only work for that IP address and hence is 1:1.
It is possible for a common name to contain a wildcard e.g. CN=*.vq.lab. This means that the certificate would work on any number of devices with an FQDN with a vq.lab suffix hence 1:M.
