Configuring Microsoft ADFS SAML2
ADFS Setup Prerequisites
ADFS Server Address
You should have the FQDN of your ADFS server available, and it be accessible to your VQ Conference Manager server.
ADFS Server Certificate
If your ADFS server service certificate is signed by an internal certificate authority, then you will need the Root CA file (without key) as a base 64 encoded X.509 .crt or .cer file.
ADFS Server Changes
You will need to add a relying party trust for VQ Conference Manager.
Server Configuration
This configuration was tested against a Windows 2012 R2 server.
- Open Microsoft Management Console by running mmc.exe in either a powershell terminal or command prompt terminal.
-
Select File > Add/Remove Snap-in and add AD FS Management
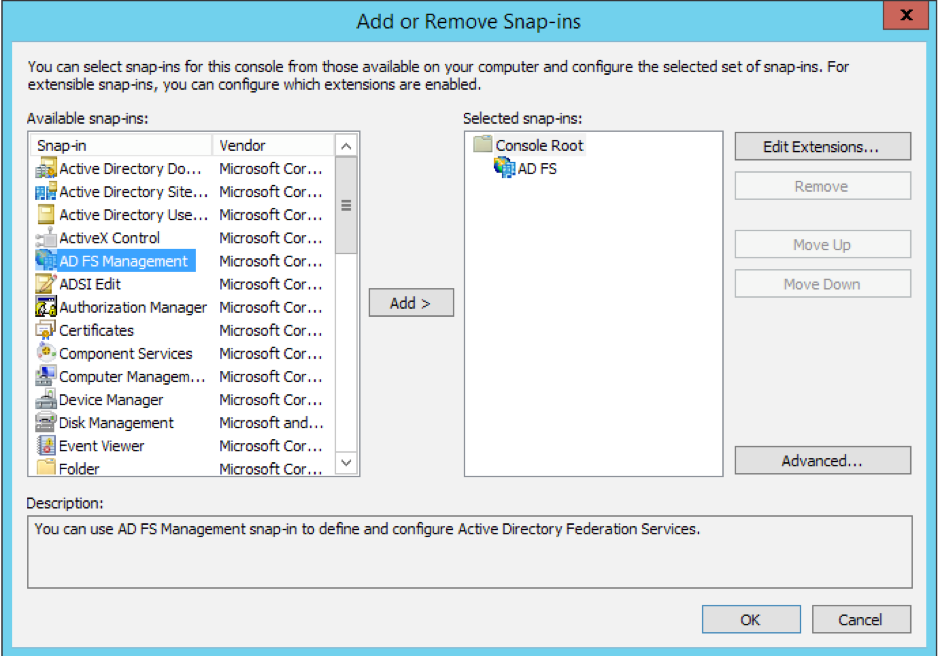
- From the Actions menu on the right hand side select “Add Relying Party Trust”
- Click “Start” on the first page of the wizard
-
Select “Enter data about the relying party manually” and click next
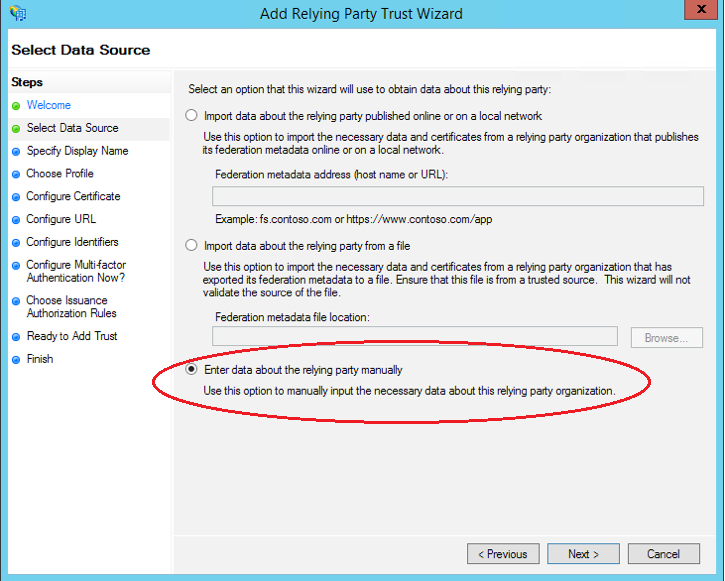
- For “Display Name” enter in “VQ Conference Manager” and add any notes you require. Then click Next
-
Select “AD FS Profile” and then click Next
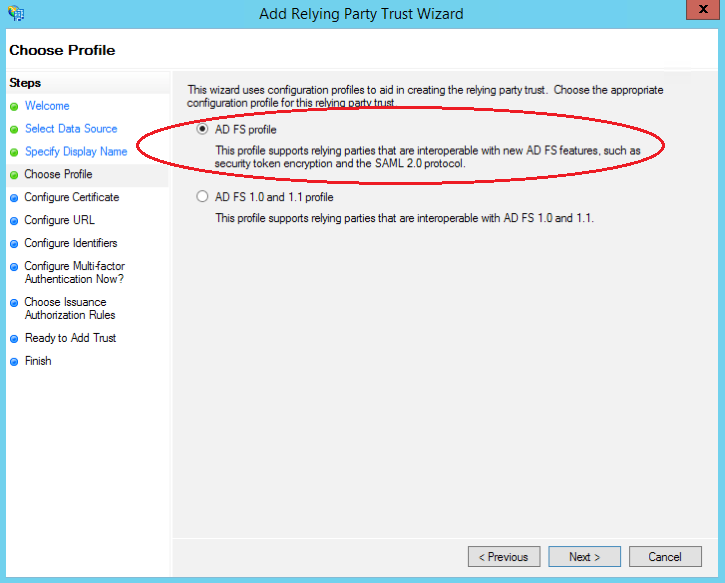
- Ignore the optional token certificate page and click Next
-
Select “Enable support for the SAML 2.0 Web SSO protocol” and enter in the following address where <login_fqdn> is the login fqdn of your VQCM installation. https://<login_fqdn>/Saml2/Acs. Click Next
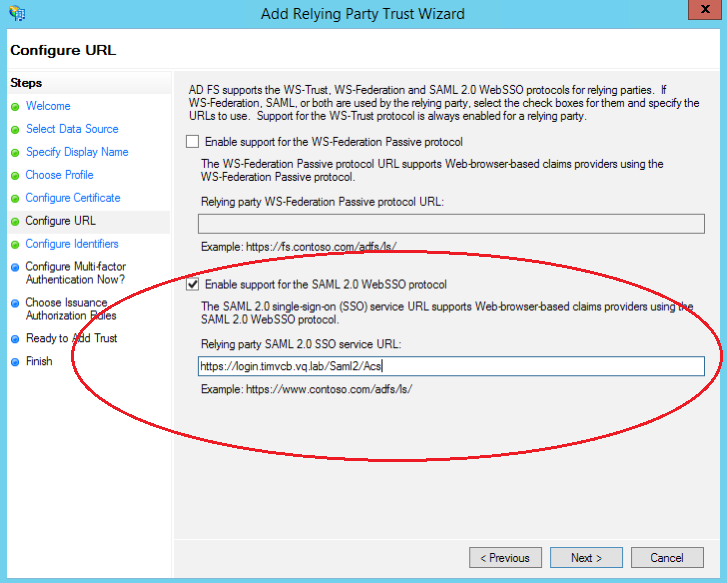
-
Enter in the following address where <login_fqdn> is the login fqdn of you VQCM installation. https://<login_fqdn>/Saml2. Click “Add” and then click Next
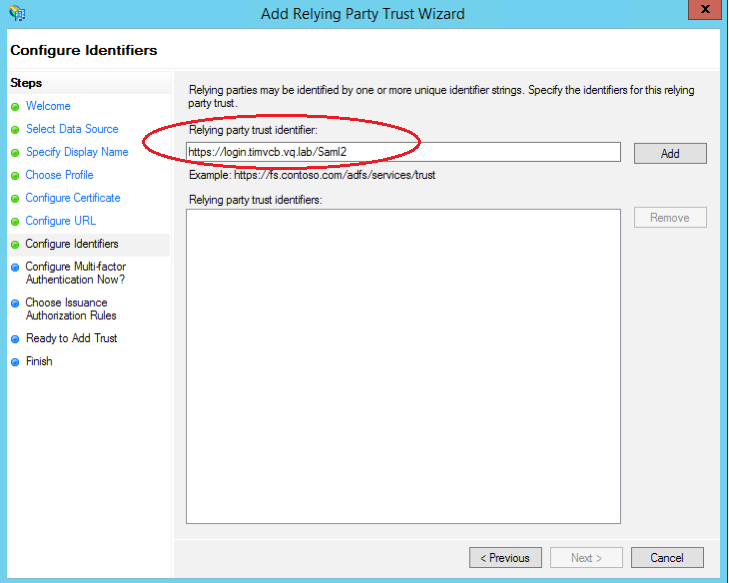
- Select “I do not want to configure multi-factor authentication settings for this relying party trust at this time” and click Next
- Select “Permit all users to access this relying party” and click Next
- Review the options you have selected and click Next . (You should not need to add any additional data on this page. The relying party trust can be configured further after initial testing if required.)
- Make sure “Open the Edit Claim Rules dialog for this relying party trust when the wizard closes” is selected and click Close
-
In the “Edit Claim Rules” window make sure you have the “Issuance Transform Rules” tab selected and click the “Add Rule” button
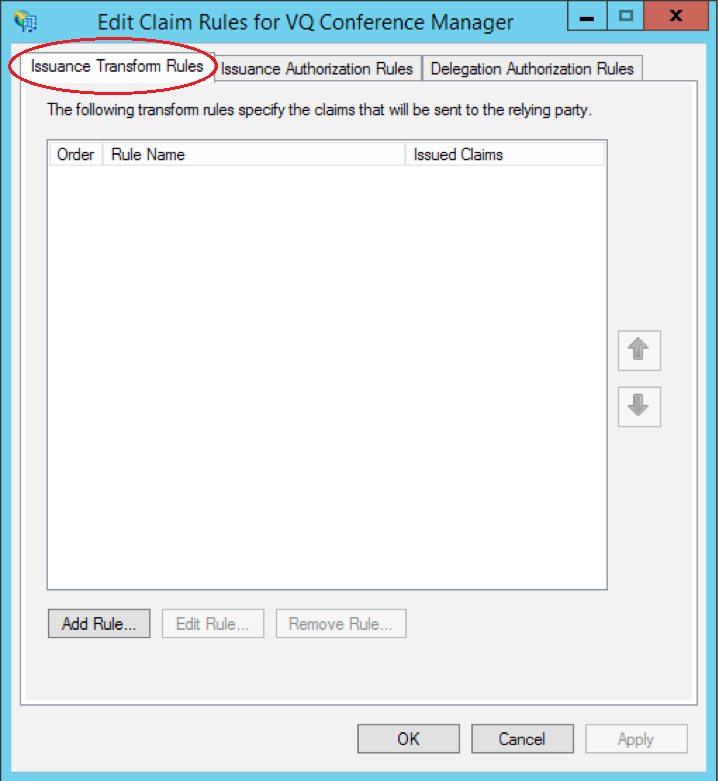
- Select “Send Ldap Attributes as Claims” and click Next
-
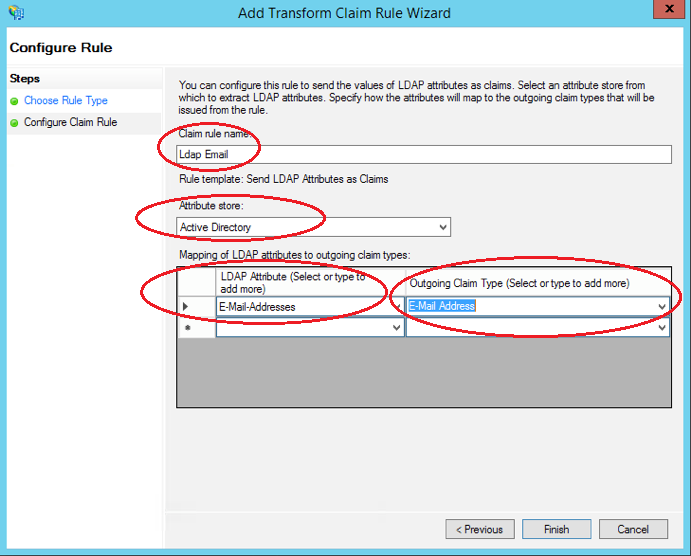
Enter in the following fields:
-
“Ldap Email” as the claim rule name
-
“Active Directory” as the attribute store
-
“E-Mail-Addresses” as the Ldap Attribute
-
“E-Mail Address” as the Outgoing Claim
Then click Finish
-
- Click Add Rule again and this time select “Transform an Incoming Claim” and click Next
- Enter in the following fields:
-
- “Email to Name ID transform” as the claim rule name
- “E-mail Address” as the incoming claim type
- “Name ID” as the outgoing claim type
- “Email” as the outgoing name ID format
-
Select “Pass through all claim values”
Click Finish

VQCM: configuring ADFS SAML2
- Navigate to the vqcm-admin interface (https://<vqcm_fqdn>:1234) and then navigate to Manage > CM Configuration
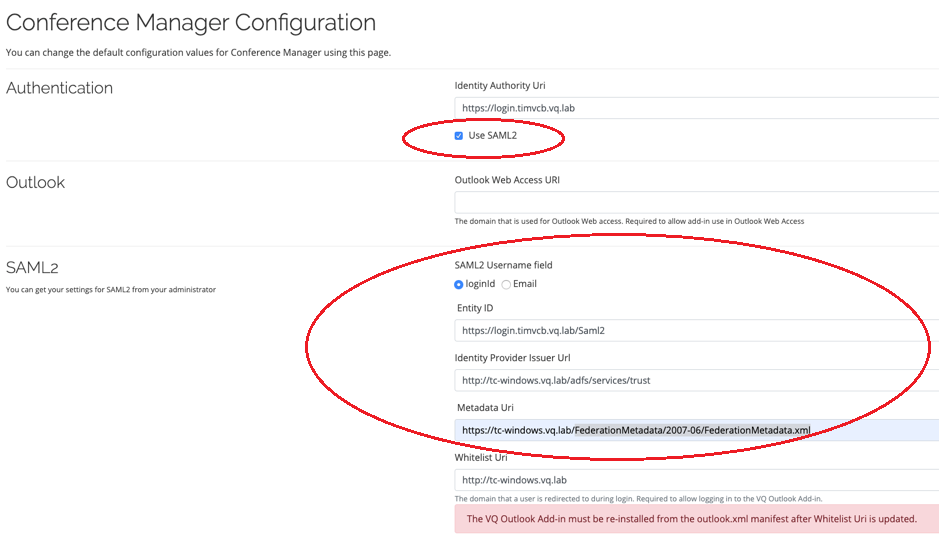
- On the CM Configuration page Check the Saml2 check box and enter the following fields where <login_fqdn> is the login fqdn of your VQCM installation and <adfs_server_fqdn> is the fqdn of your adfs server:
- “loginId” as the SAML2 username field.
- https://<login_fqdn>/Saml2 as the Entity ID
- http://<adfs_server_fqdn>/adfs/services/trust as the Identity Provider Issuer URL
https://<adfs_server_fqdn>/FederationMetadata/2007-06/FederationMetadata.xml as the Metadata Uri
Then click Save
You should now be able to navigate to the VQCM FQDN and login using your windows credentials.
Things to watch out for
- Make sure you are using the mail ldap attribute as the username field for your users in the ldap config. This will then be matched against the Name ID claim from the adfs server which also contains the ldap mail attribute.
-
If your ADFS server service certificate is signed by an internal certificate authority, then you will need VQCM to trust your internal CA. This can be done from the "trusted certificates" page, described the chapter Managing Trusted Certificates.
Testing the ADFS configuration
From VQCM 3.7, a tool that allows the ADFS configuration to be tested is pre-installed onto the VQ VM. The tool parses the metadata and certificate from the ADFS server and then configures the VQCM VM to work with that ADFS server.
The process for using the tool (troubleshoot-adfs) is:
- Configure the ADFS server as documented above
- If you encounter errors after configuring ADFS, run the troubleshoot-adfs script (via ssh onto the VQ CLI)
The tool picks up the ADFS configuration from VQCM and then will instruct you of any corrections you need to make to the ADFS configuration.
For assistance, please contact support@vqcomms.com.
Alternative Configuration
If you wanted to use another unique ldap attribute other than email to use as the Name ID claim then you could do this by modifying the 2 claim rules to use this alternative ldap attribute instead of the email attribute. You would also need to configure your ldap config in VQCM to use this alternative attribute as the username field.
