Configuring VQ-Admin to work with Okta, Duo and OneLogin SAML2
The process required for Okta, OneLogin and Duo is essentially the same: The first step is that the application is registered for use with the SAML2 Service Provider. The Registration process requires details on the Identity (certificate based FQDN URI) that the application uses to identify itself and provides a URI (certificate based FQDN) that the application will use to interface with the SAML2 Service Provider. In the case of Okta, the Service Provider also provides a Metadata URI that the application should use to obtain details about accessing the SAML2 service.
On enabling SAML2, the SAML 2 text boxes will be enabled.
The Identity ID is the Login FQDN for your VQCM with a postfix of “/Saml2”. For example, if your login FQDN is login.vqcm.mydomain.com, the Identity ID needs setting to https://login.vqcm.mydomain.com/Saml2.
CAUTION: We strongly recommend copy/pasting the Entity ID from VQCM into your SSO provider’s settings to reduce the risk of hard to identify problems.
The certificate used to sign the certificate used by VQCM needs to be from a public Certificate Authority. For customers who use privately generated certificates from a non-public root, the root certificate will need to be added to VQCM’s public certificate store via the VQCM-Admin portal.
Summary of differences between Okta, OneLogin and Duo:
• OneLogin and Duo require the Provider Issuer URI only
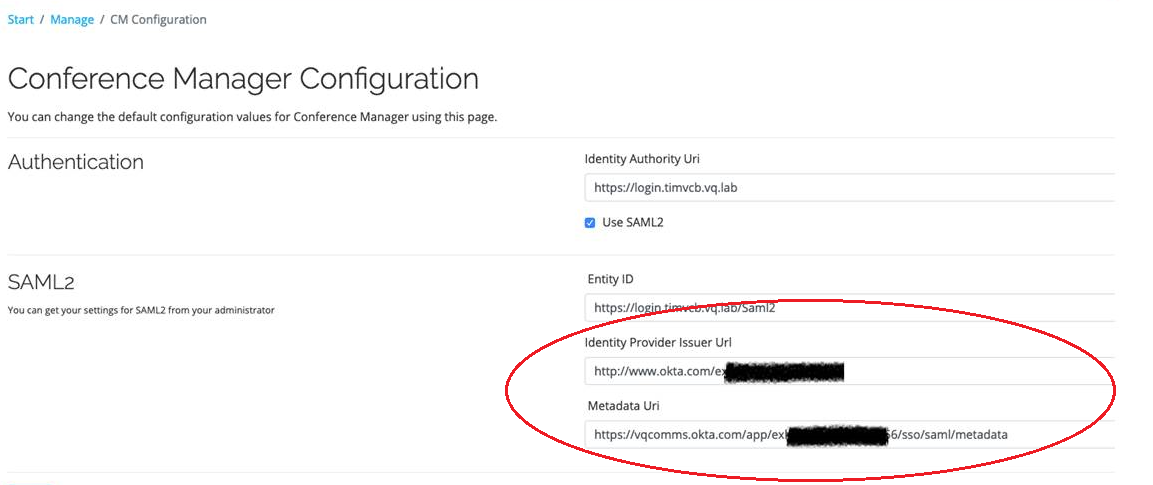
• Okta requires both the Provider Issuer URI and Metadata URI
Example Okta SAML 2 settings:
Example OneLogin/Duo settings:
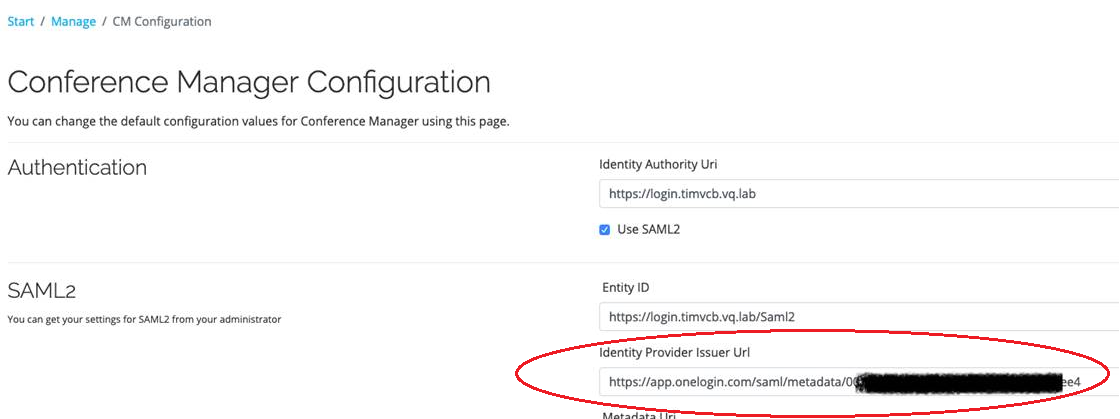
Note that OneLogin and Duo automatically resolves the Metadata URI as part of the handshake that takes place between the VQCM Identity Server and the OneLogin/Duo Identity Provider.
Whitelist for the Outlook Add-in
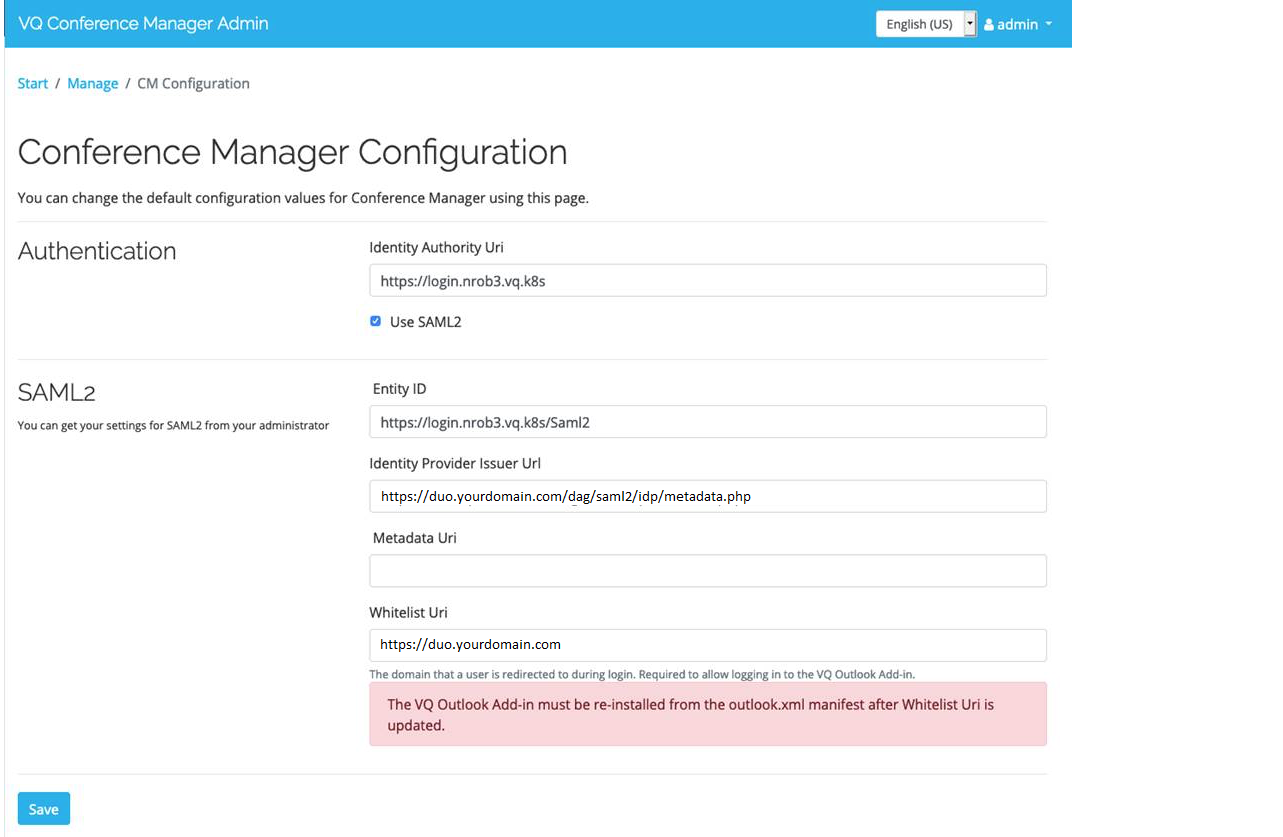
The "whitelist" is a list of good URLs that the Outlook Add-in will talk to, preventing it rejecting the request because of the risk of "cross site scripting".
The "whitelist" needs setting when using an external autherisation provider (i.e. normally anyone using SAML2). It needs setting to the domain that users get redirected to, to login.
For example:
https://yourdomain.okta.com would be the Okta domain
https://yourdomain.onelogin.com would be the onelogin domain
As the first part of the domain is different for every customer it needs setting for each customer.
An example with values for a Duo setup: