Managing Trusted Certificates
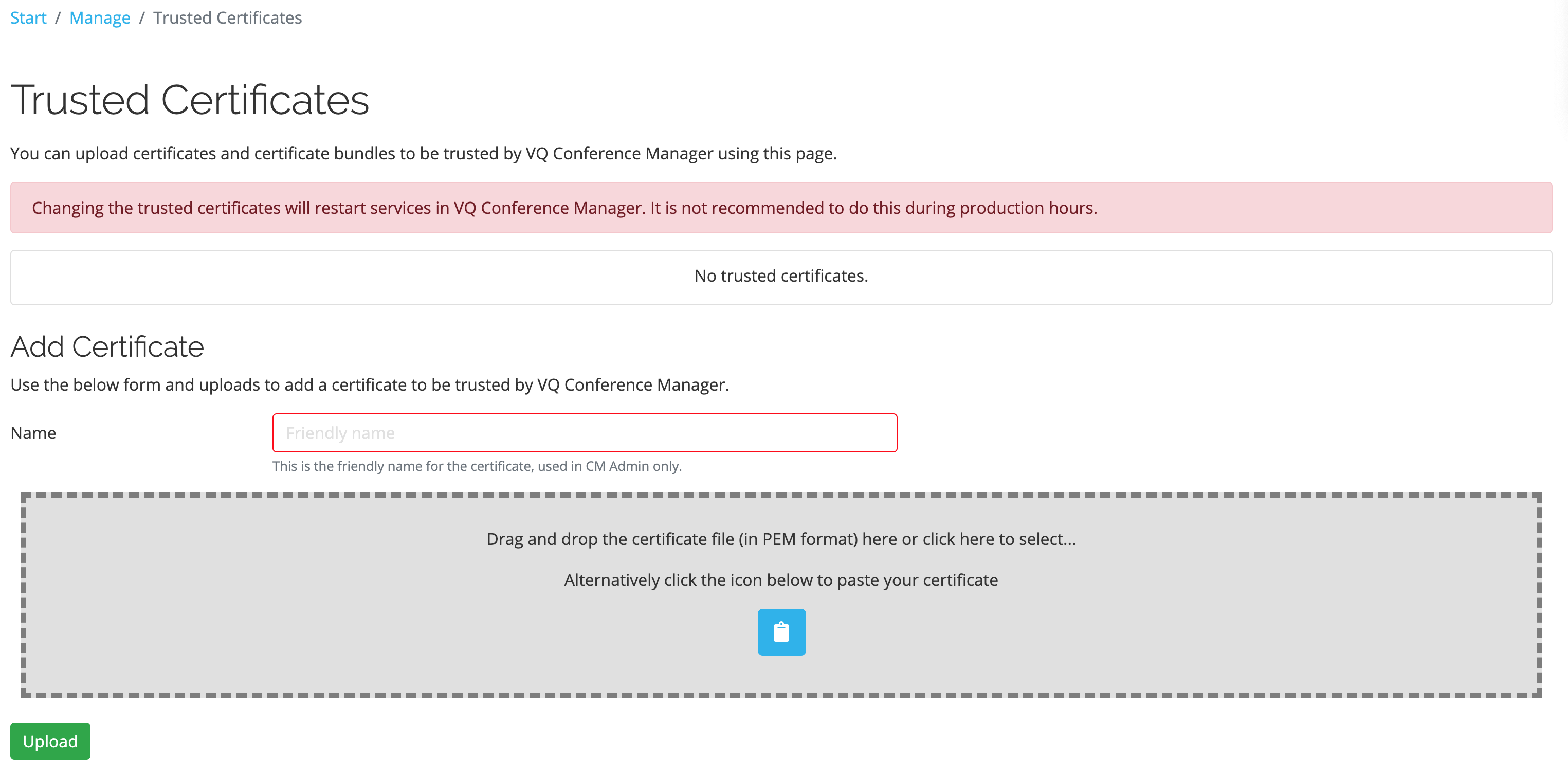
Trusted Certificates
In environments where certificates do not come from a Certificate Authority, certificates can be added to be trusted by VQ Conference Manager.
From VQCM-Admin navigate to Start -> Manage -> Trusted Certificates
Uploading Root Certificates
We've added the ability to upload trusted certificates. There are two formats: pem and pki. Windows uses pki format certs and linux based systems typically used pem.
Why is this beneficial?
Part 1: What’s a Trusted certificate?
A certificate is one or more certificates chained together. Each certificate is issued by somebody (typically an organization).
When a certificate is used, the list of certificates in the chain are checked. Does each certificate come from a Certificate Authority (CA) that is known and trusted?
Public CAs (company’s like Digicert, GoDaddy etc) issue certificates that are also based on a chain; the first certificate in the chain being one of a handful that are globally managed and trusted. This small set of “root” certificates are pre-loaded into the Trust store of the Operating System hosting VQ (and the certificate store of all other operating systems and therefore PCs, iPhones, Ipads etc on the planet).
So, the certificate chain checks can “walk” their way through the certificate chain and validate that each certificate in the chain comes from a trusted Certificate Authority.
Part 2: Why is this new functionality a good thing?
Some organizations (for example, Defense Departments or Financial Enterprises) have their own Root Certificate. It’s the basis for all Certificates signed with that organization.
The new functionality is beneficial because it allows customers with their own Root Certificate to easily upload it into the trusted certificate store of the operating system hosting VQ. The mechanism also allows intermediary certificates to be uploaded. The certificate chain editor allows the sequence of certificates to be correctly sequenced; it also shows the certificate subject and issuer. It is therefore much easier to assemble the certificate chain into the correct sequence.
We also added the ability to paste a certificate into the certificate editor.
Here’s screenshot of the certificate editor for the vqcomms.com “wildcard” certificate on InternalAM:
From VQCM-Admin navigate to Start -> Manage -> Certificates
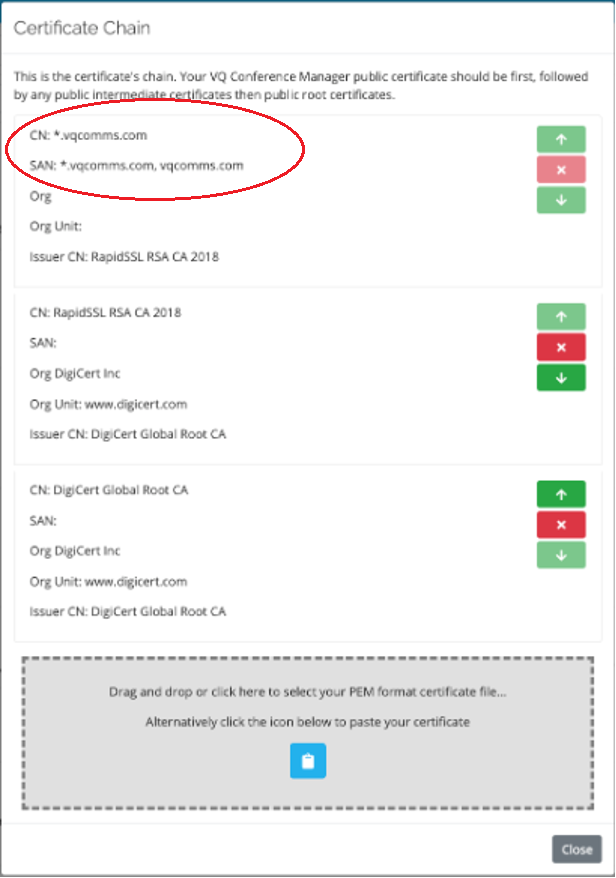
CN: Common Name: (Human readable name)
SAN: Subject Alternative Names: In this case, you can see the * in front of vqcomms.com. The certificate can therefore be used for internalAM.vqcomms.com, whizzystuff.vqcomms.com etc.
You can see how the chain goes all the way back to digicert.

If you then look at the “default” cert chain:

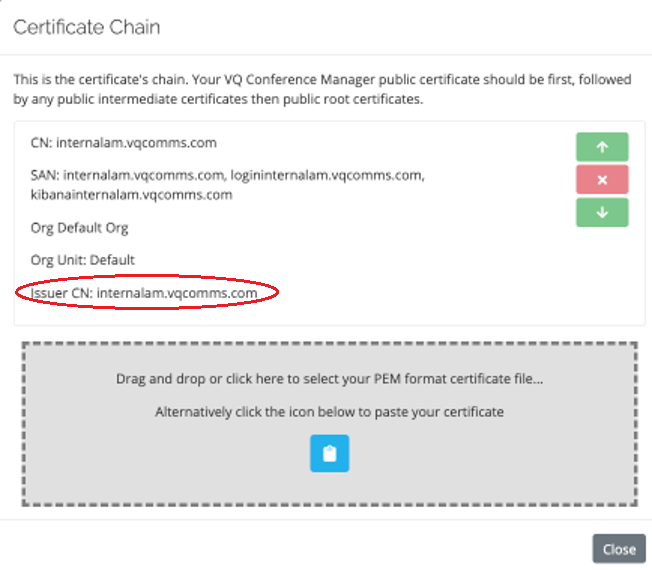
You can see the issuer was VQ. This is the self-signed cert that the software generates for itself at install.
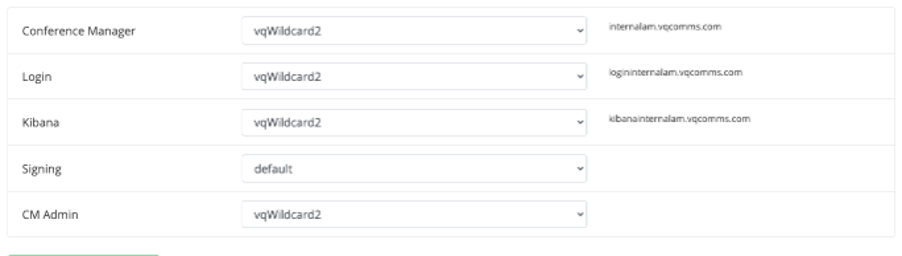
All these cert tools are incredibly useful if you are onsite on, for example, a defense site and need to discover and then patch together the certs into a valid chain. It can be massively time consuming because typically the certs have been downloaded as a block without any details; the re-assembly can be truly painful.
This functionality doesn’t look much like a conferencing tool but for the commissioning engineers, it’s a big deal (and we’ve had really good and appreciative feedback on it).
